The Top Trending Vulnerabilities of Q2 2024
The Top 12 most critical vulnerabilities that trended during Q2 2024, and 5 other trends you should know about

(and some other interesting stuff we think you should know about)
“Eugh, please no ‘thought leadership’. Just give me the list that I need to fix”
I know you thought it. Our CEO, Matt, even told me you would.

Fine. We’ll skip the ChatGPT generated intro about the ever-evolving world of cyber security and dive straight in.

The Top 12, Most Critical Vulnerabilities of Q2
Why 12?
I promise we are not trying to be contrarians. From the 128 unique vulnerabilities that were added to the Cytidel Spotlight during Q2, 12 stood out because they matched all of the following criteria:
- 'Significant' Risk Rating on the Cytidel Vulnerability Intelligence platform
- Trended prominently across news and social media
- EPSS (Exploit Prediction Scoring System) score greater than 90%
- Associated with an active exploit or zero day
- Have one or more proof-of-concepts
- Were added to CISA Known Expoloited Vulnerabilities (KEV) Catalog
The top trending vulnerabilities in order of EPSS
| CVE | Vendor | CVSS | EPSS | Cytidel Risk Rating |
|---|---|---|---|---|
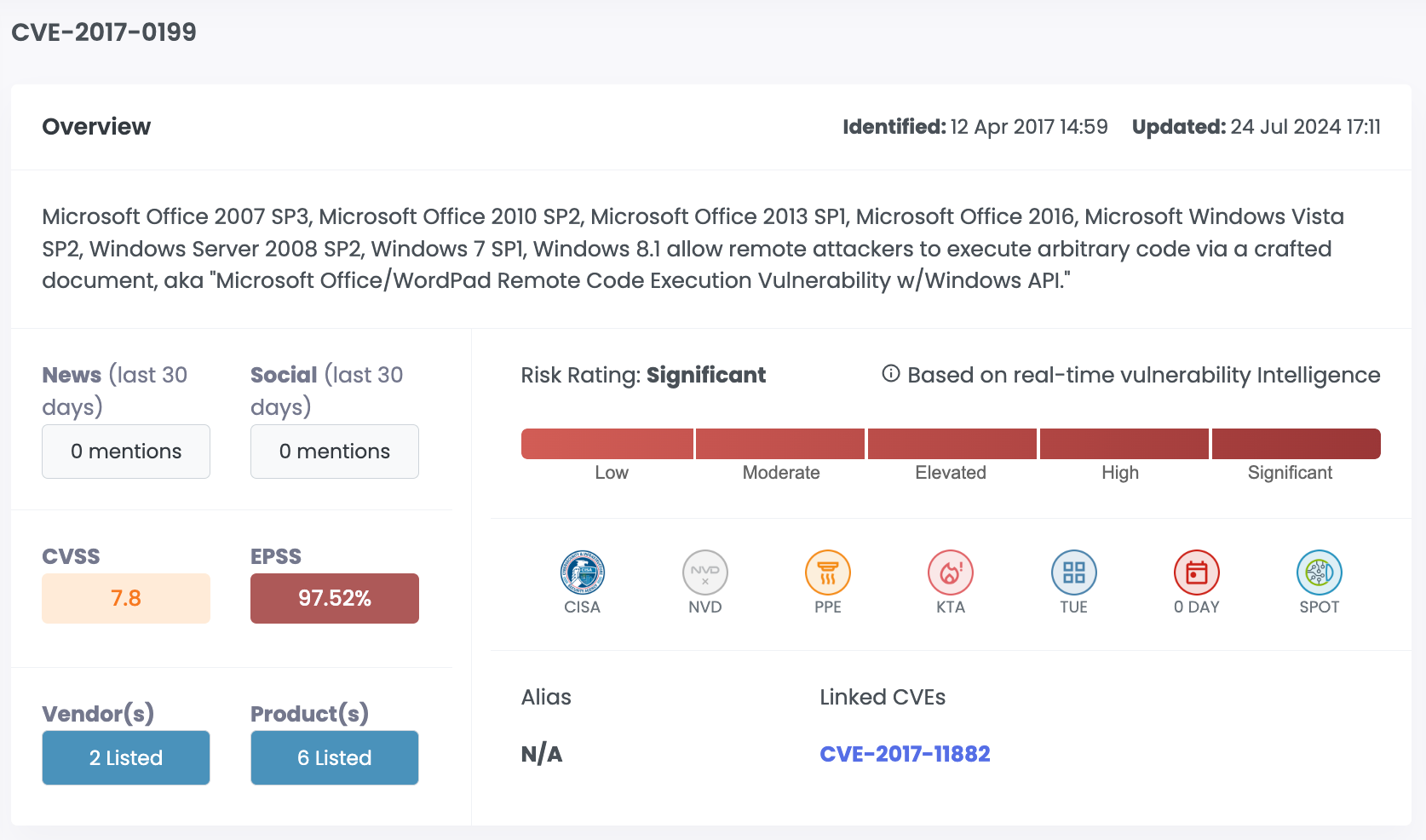
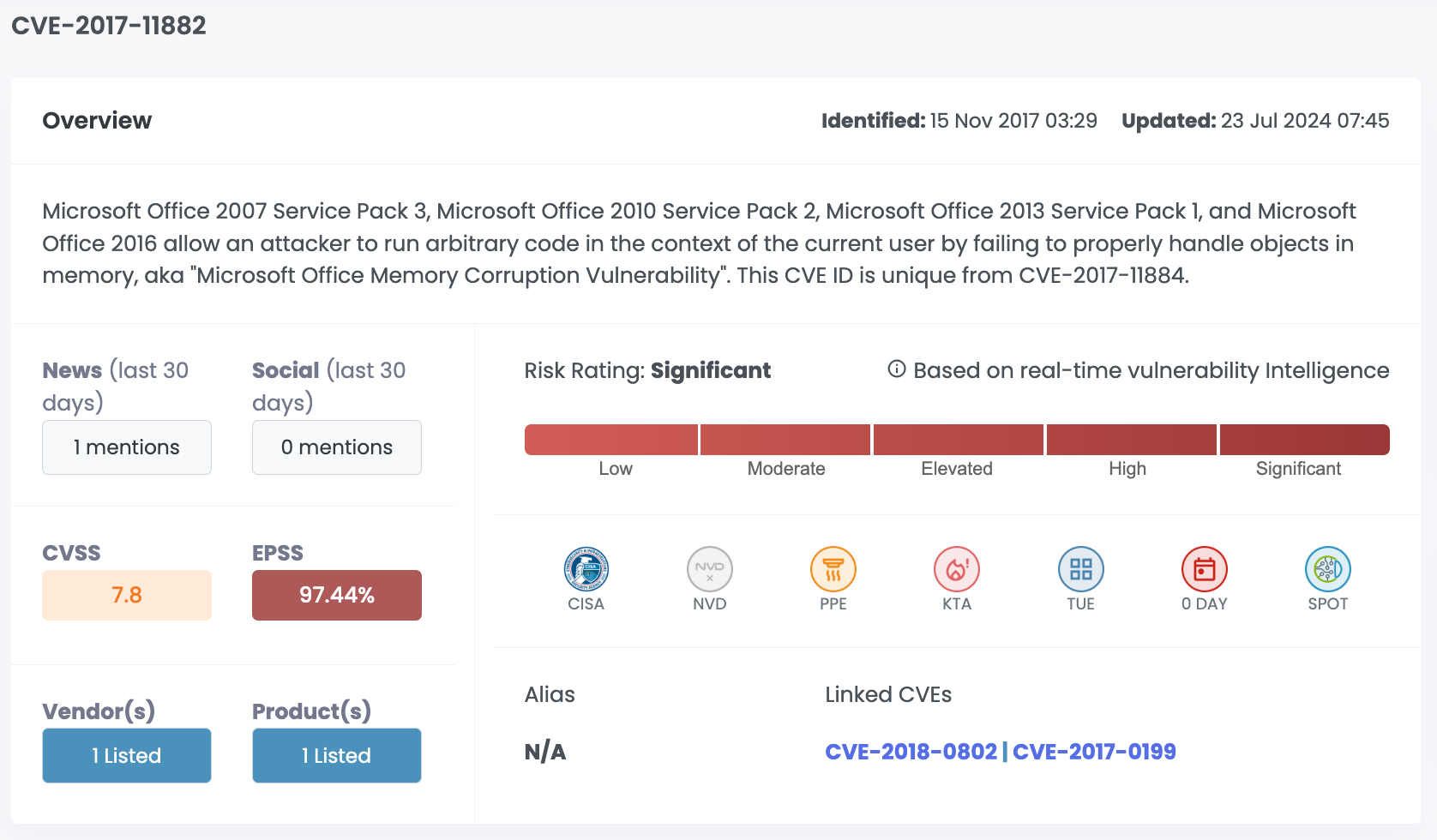
| CVE-2017-0199 | Microsoft Office | 7.8 | 97.45% | Significant |
| CVE-2017-11882 | Microsoft Office | 7.8 | 97.44% | Significant |
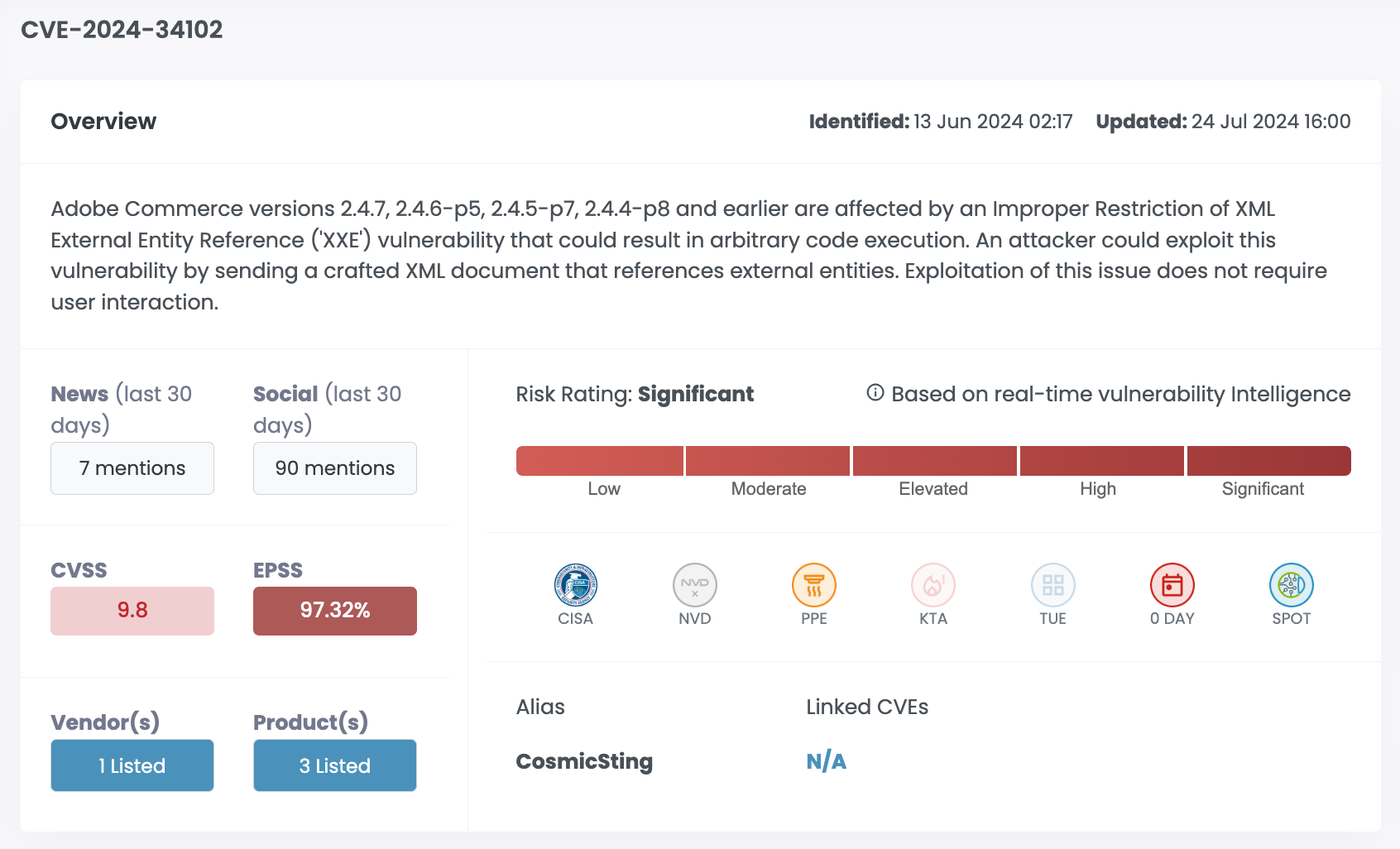
| CVE-2024-34102 | Adobe Commerce | 9.8 | 97.32% | Significant |
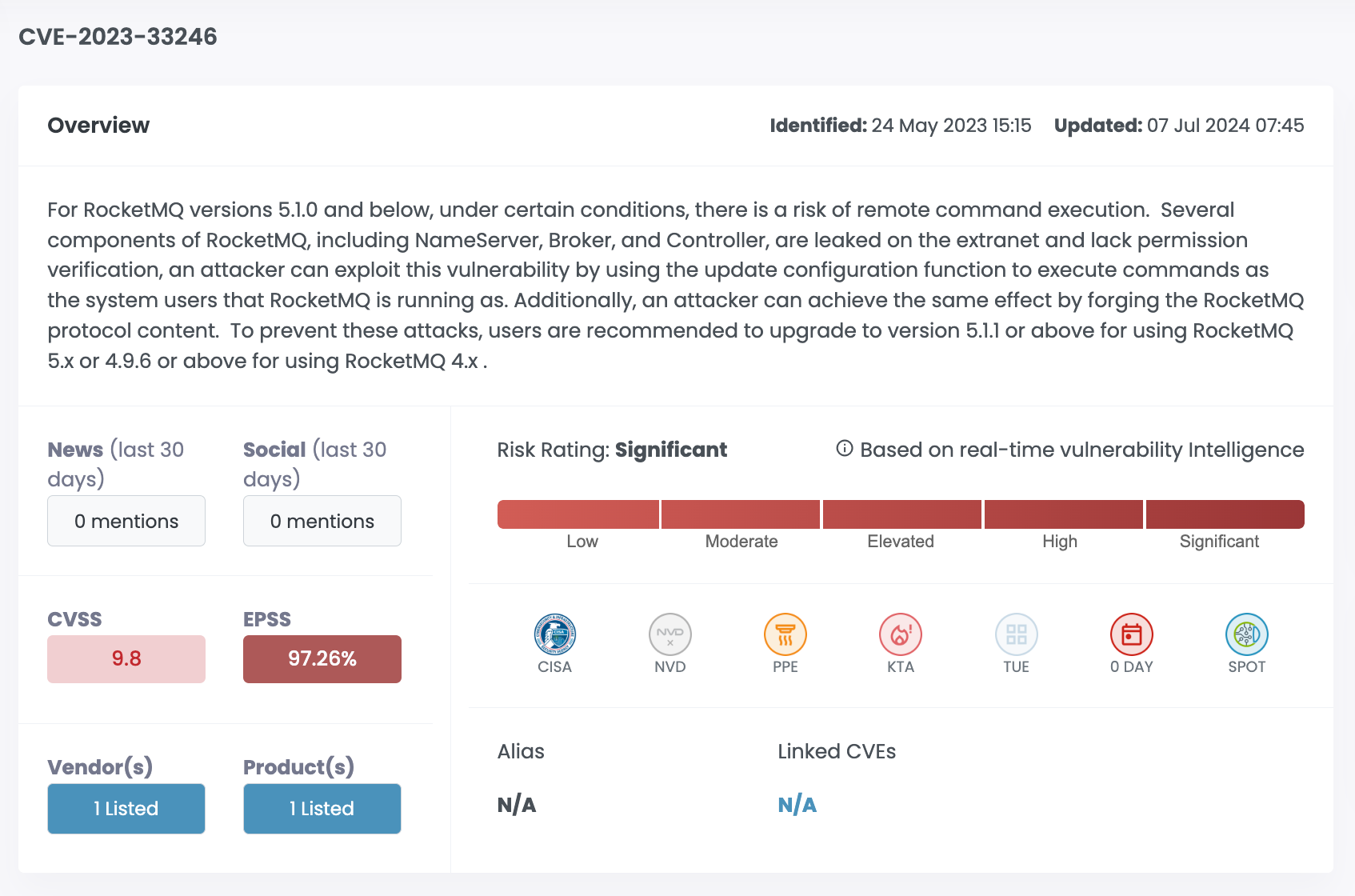
| CVE-2023-33246 | Apache RocketMQ | 9.8 | 97.26% | Significant |
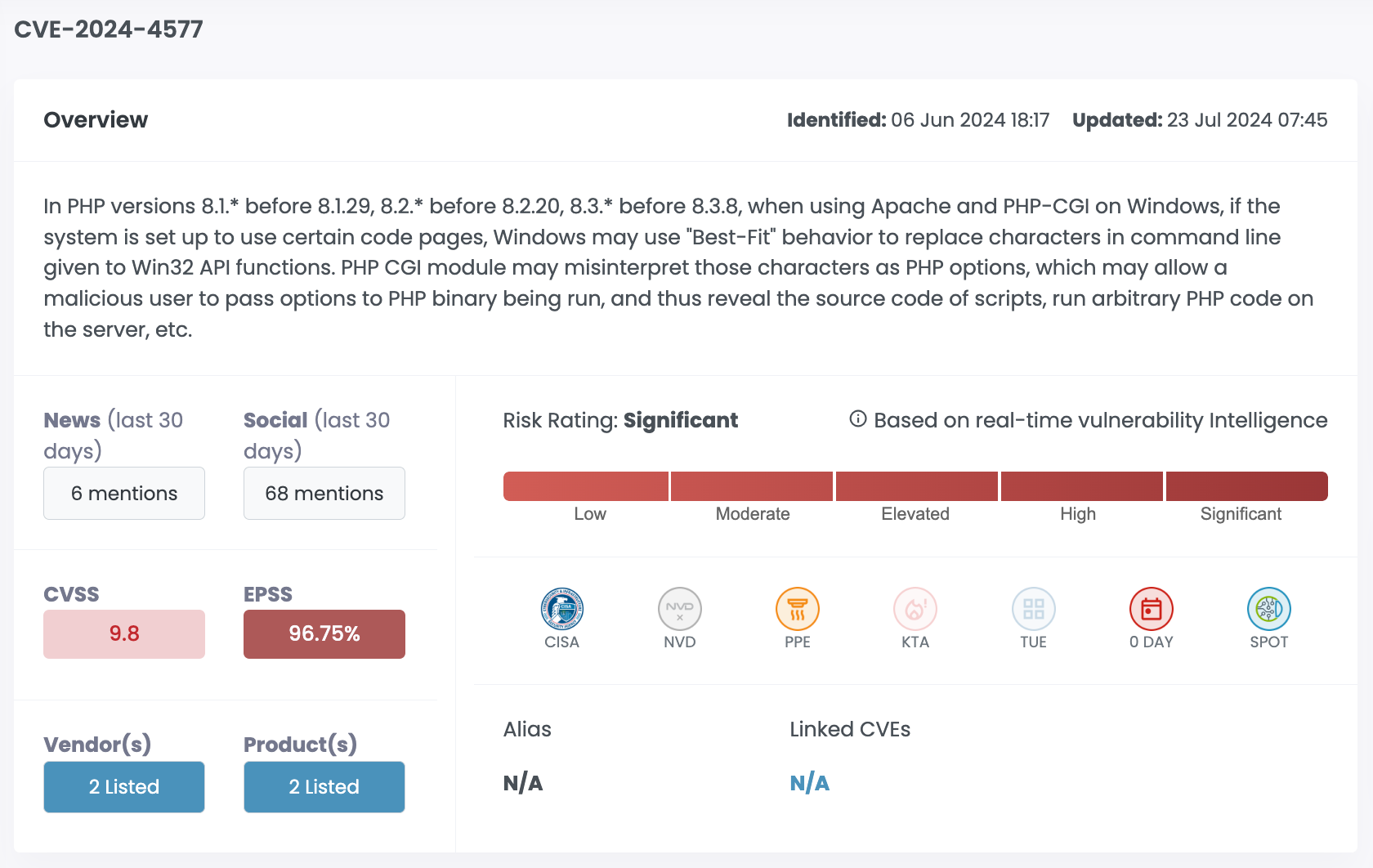
| CVE-2024-4577 | PHP | 9.8 | 96.75% | Significant |
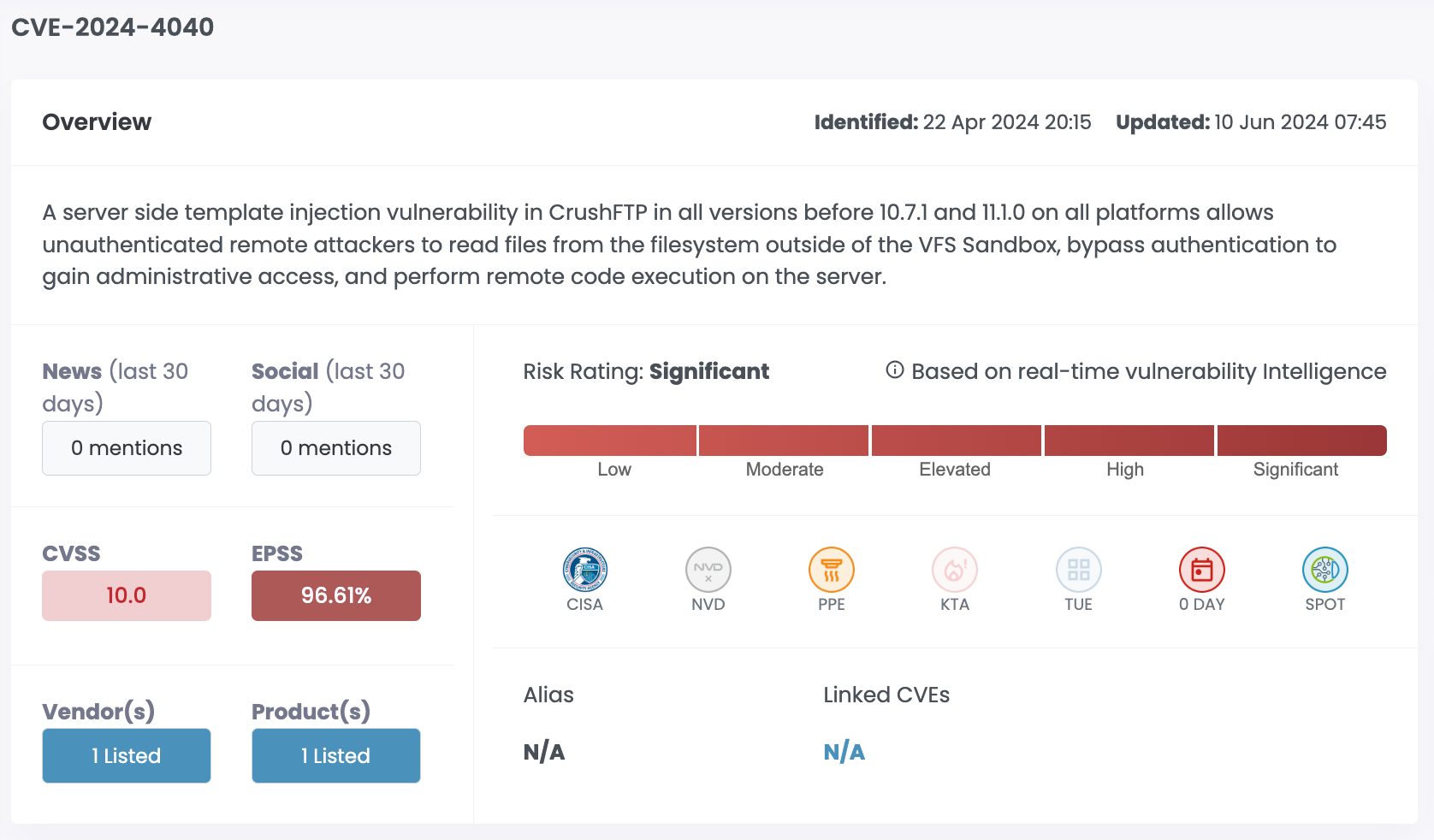
| CVE-2024-4040 | CrushFTP | 10.0 | 96.61% | Significant |
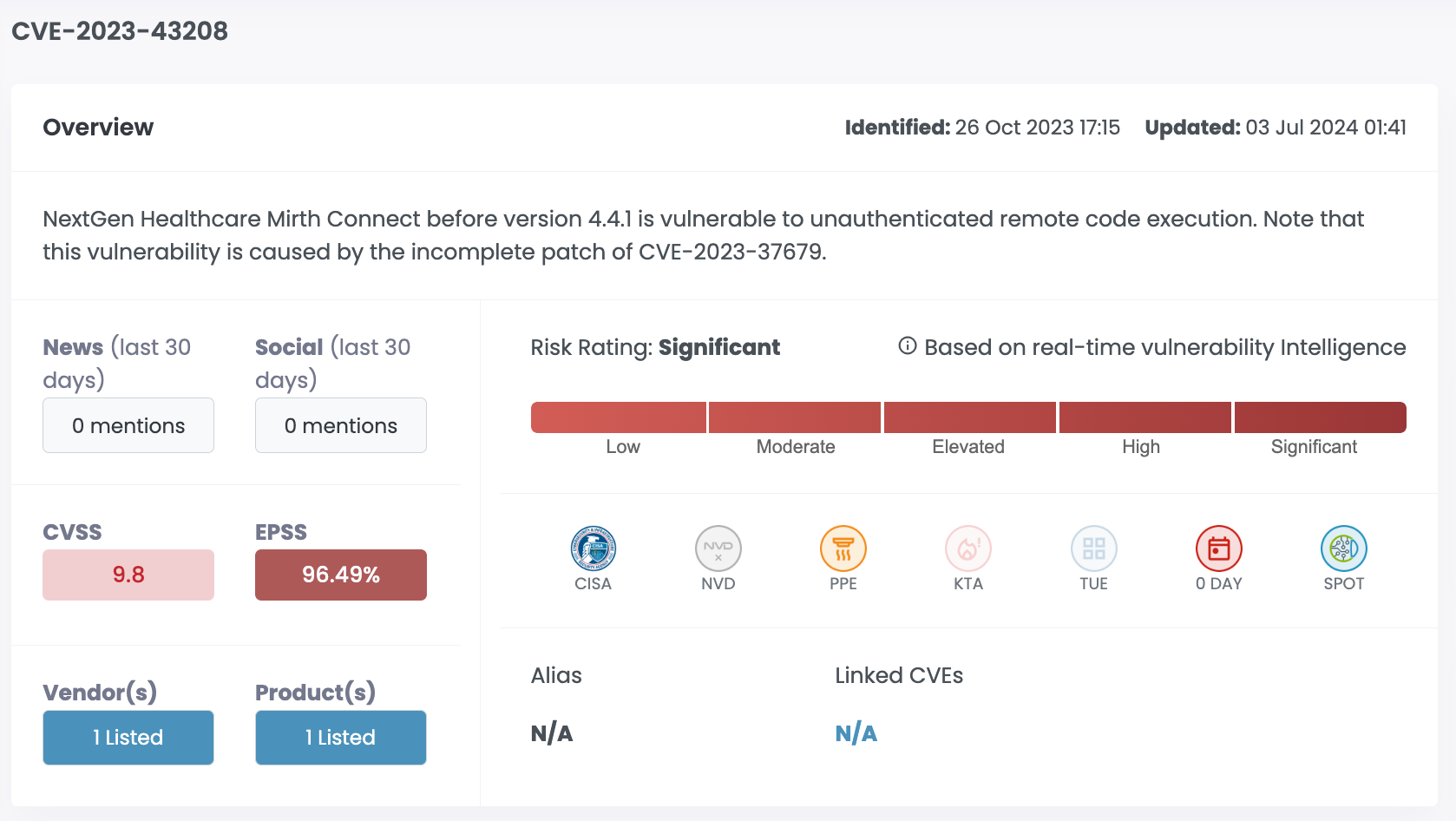
| CVE-2023-43208 | NextGen Healthcare Mirth Connect | 9.8 | 96.49% | Significant |
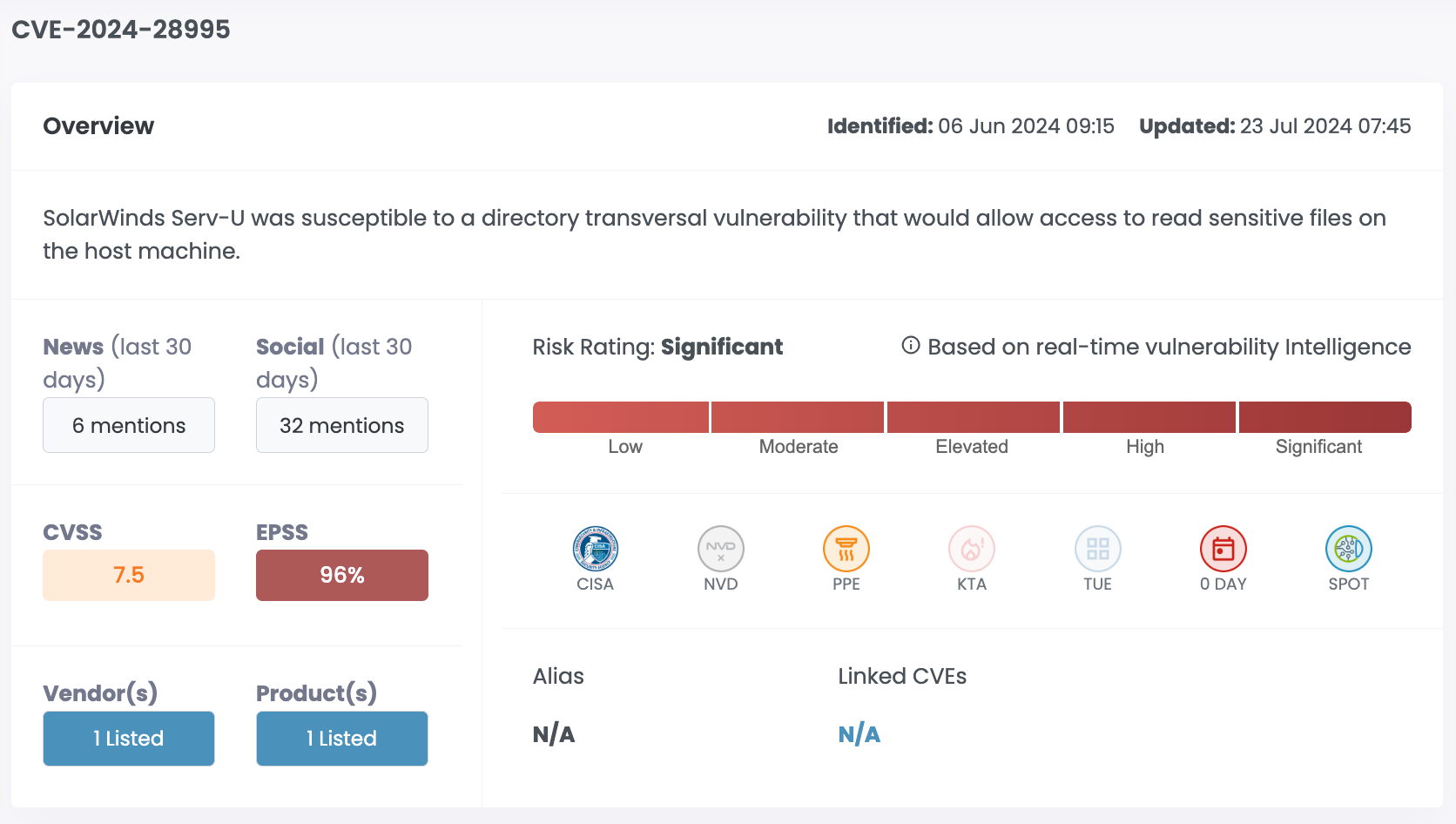
| CVE-2024-28995 | SolarWinds Serv-U | 7.5 | 96.00% | Significant |
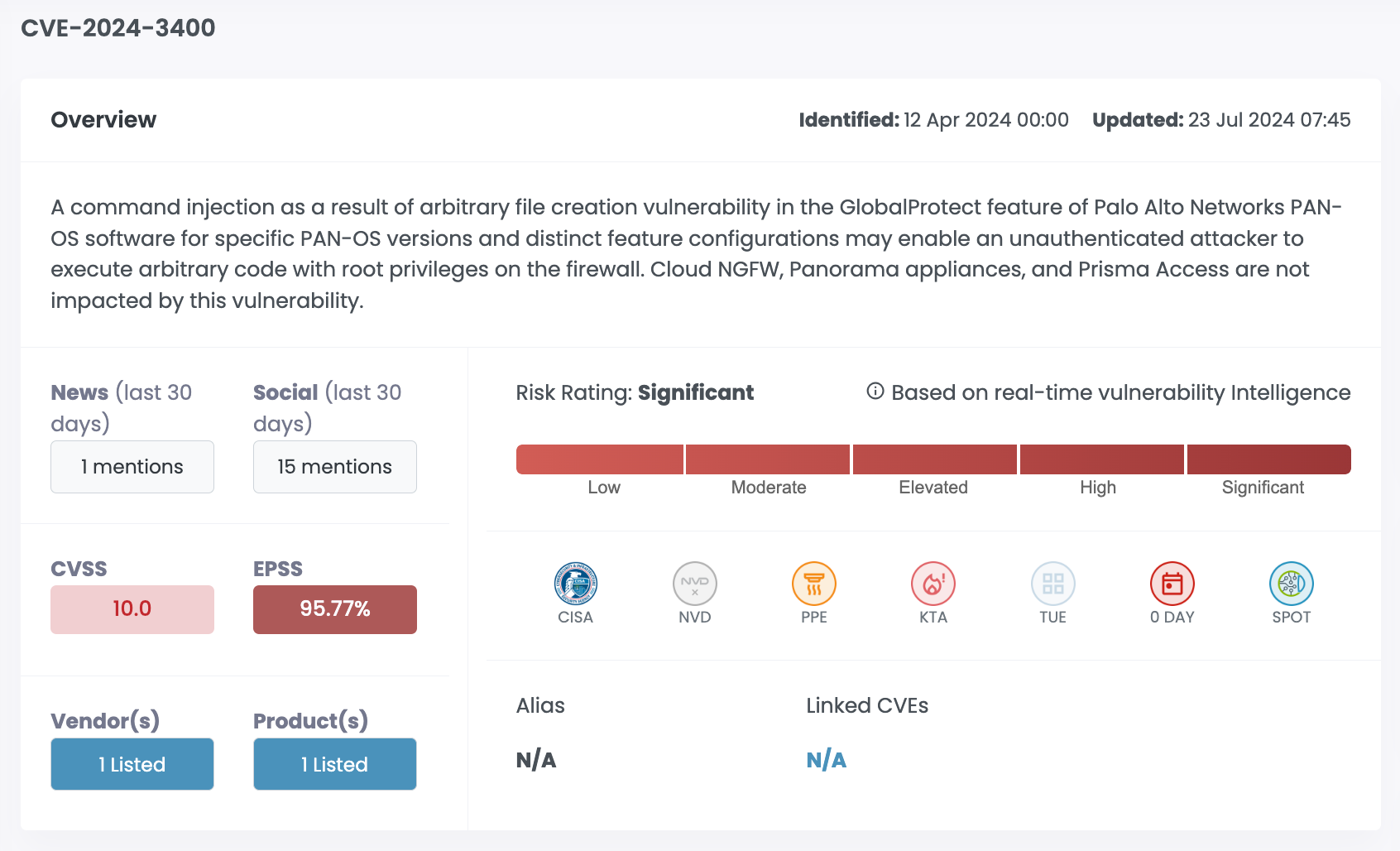
| CVE-2024-3400 | Palo Alto PAN-OS | 10.0 | 95.77% | Significant |
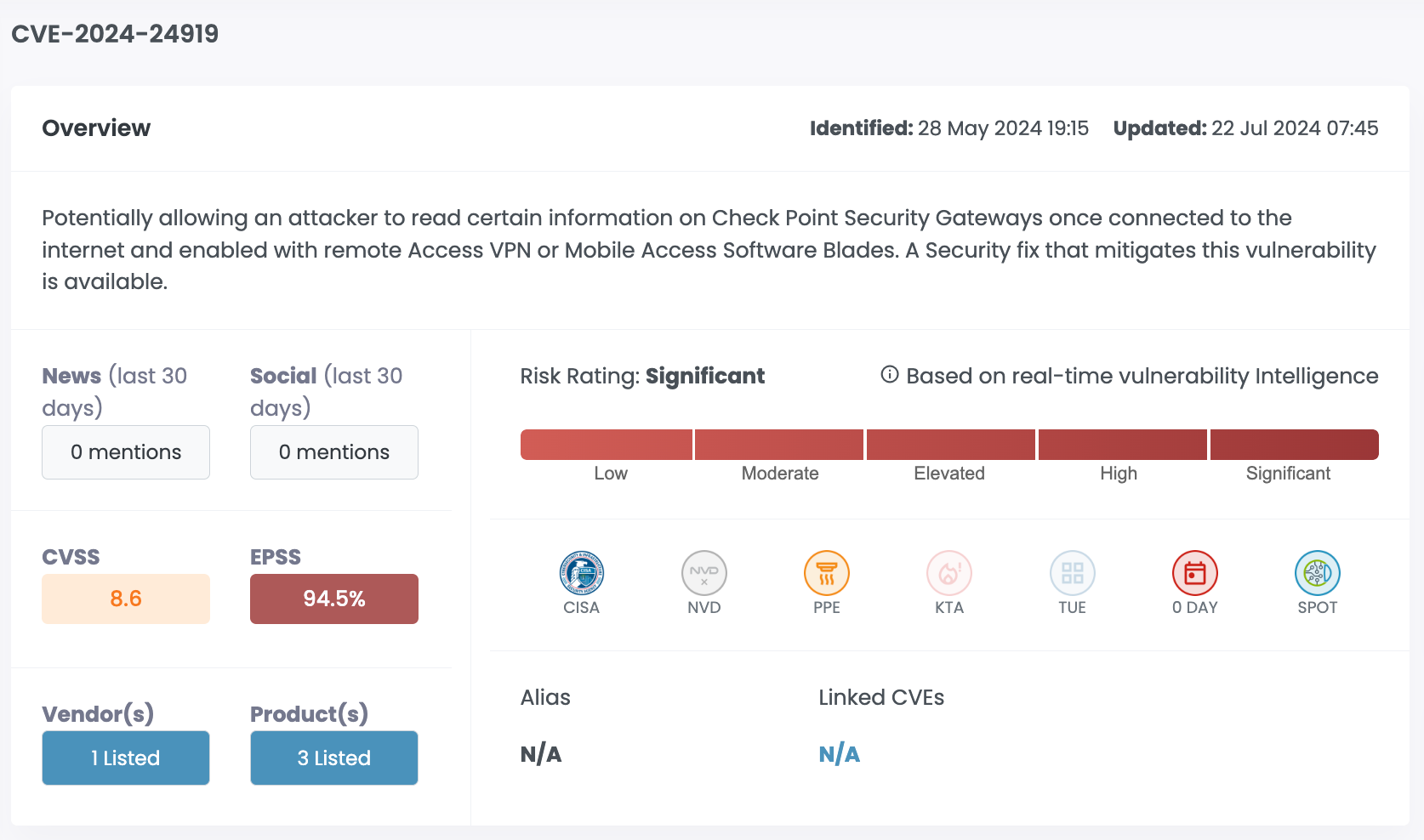
| CVE-2024-24919 | Check Point Security Gateways | 8.6 | 94.50% | Significant |
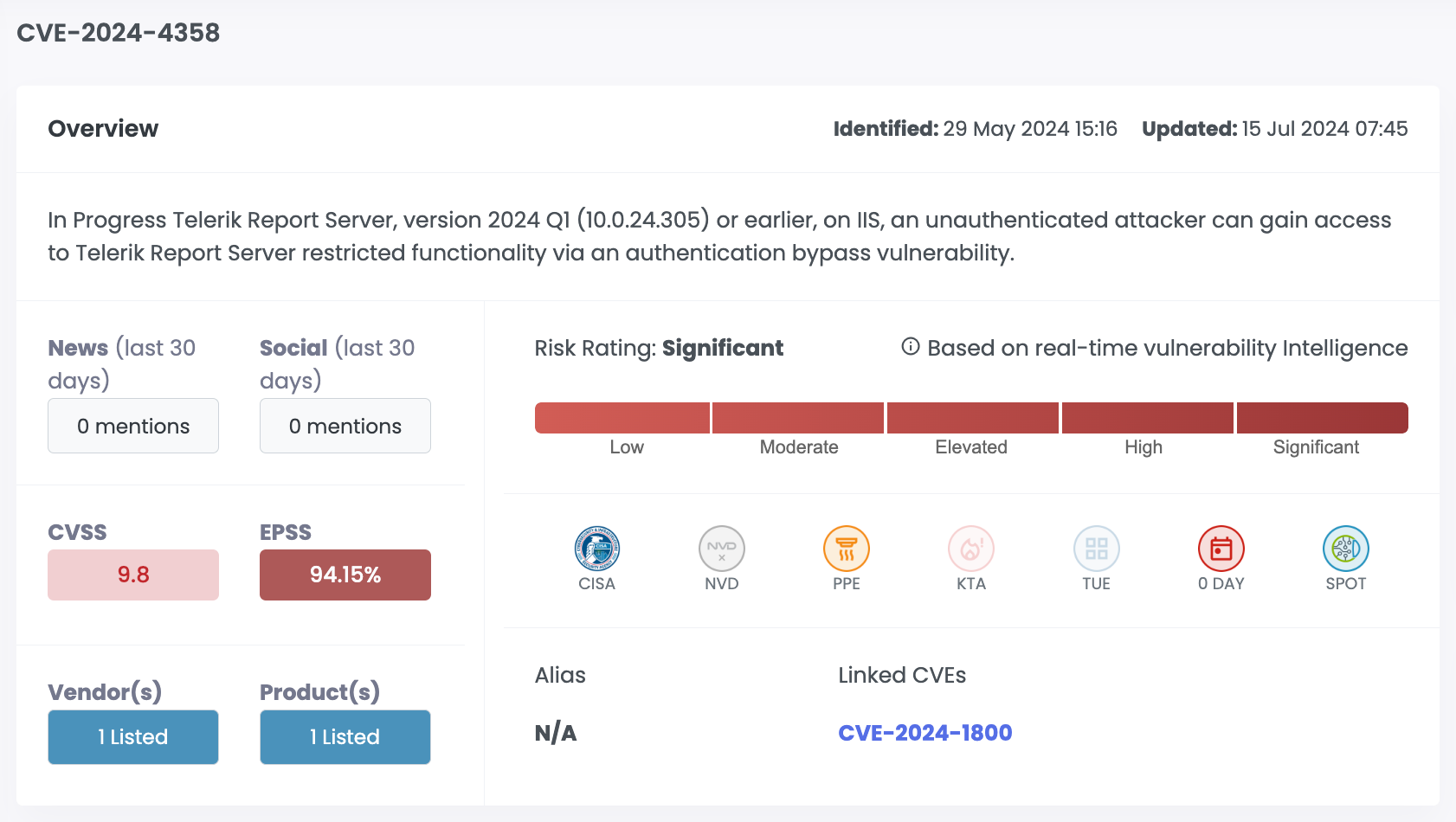
| CVE-2024-4358 | Progress Telerik Report Server | 9.8 | 94.15% | Significant |
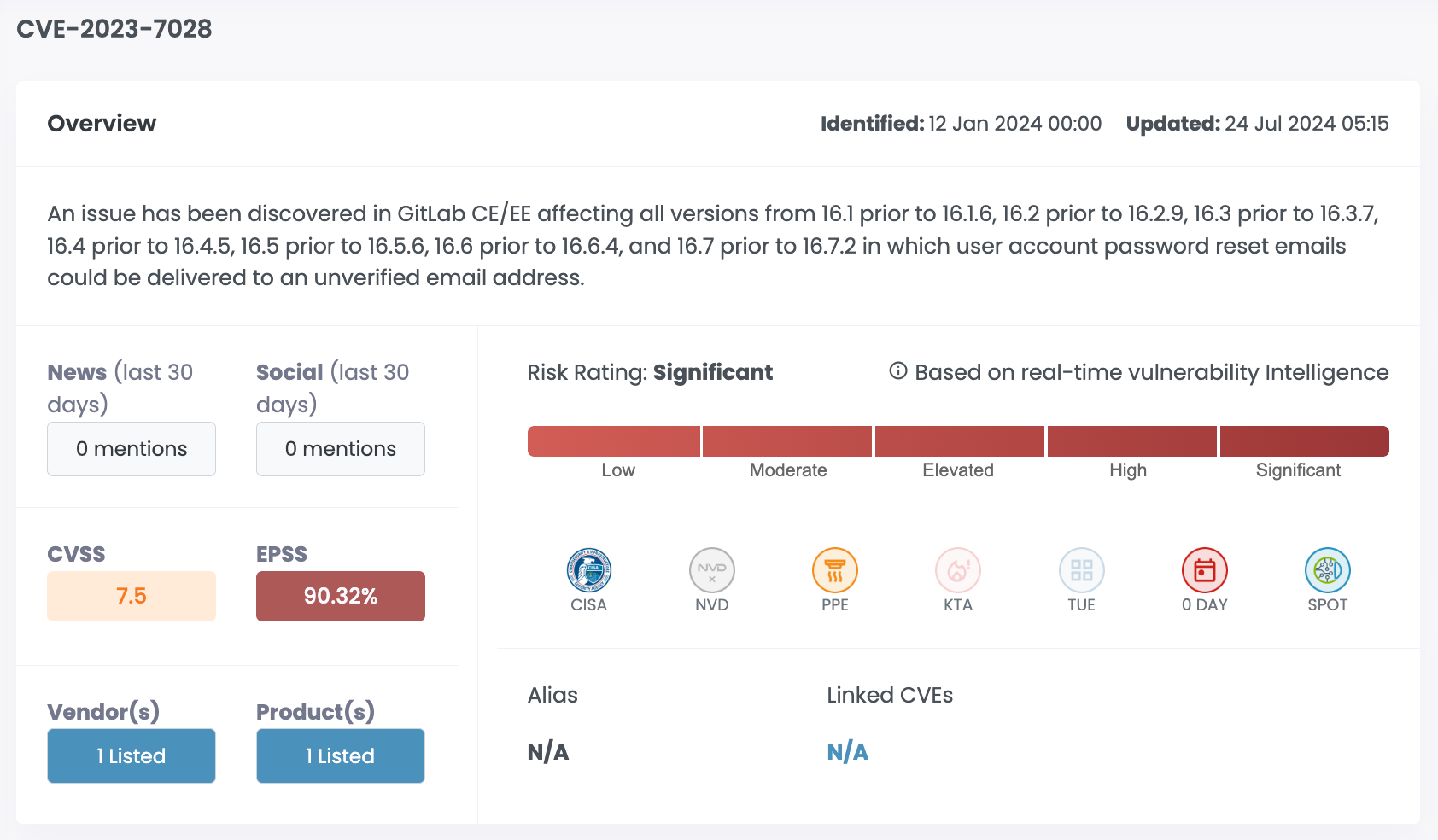
| CVE-2023-7028 | GitLab | 7.5 | 90.32% | Significant |
View CVE Profiles
The Other Stuff We Think You Should Know About
Now that we've given you the top trending vulnerability list, here's some trends we've noticed that we had to get off our chest. And admittedly, it strays shamefully close to 'thought leadership'.

1. The level of new vulnerabilities is up 40% year-on-year growth for 2024
Despite it only being July 2024 at the time of writing, we have already seen over 22,000 new vulnerabilities published in 2024, giving us over 40% growth YoY from the record high number of 28,000+ published CVEs (Common Vulnerabilities and Exposures) in 2023.
Why are there more and what does it mean for you?
One reason is simply the fact that there are more vendors now registered as CVE Numbering Authorities (CNAs), meaning there are more companies actually declaring software vulnerabilities.
There are currently 395 registered CNA’s (July 2024), with 50 of these being registered since January 2024. That’s almost a 15% increase in the numbers of organisations registering CVE’s since the beginning of the year.
This is great, on one hand, as it provides greater transparency between vendors and customers, enabling better visibility of the risk and exposure that you are living with.
However, there are instances of CNAs declaring vulnerabilities in a manner that is adding more mud to the already muddy, muddy vulnerability prioritisation waters.
For example, Microsoft announced in June that they would begin assigning CVE ID’s to cloud vulnerabilities in an effort to improve transparency. While this is great for the security community to understand their potential historic exposures, these CVE’s require no customer action. This will result a significant uptick in CVE numbers that in reality doesn't correspond to an actual uptick in risk that organisations can address or action.
Security teams that have traditionally reported on their exposure solely based on CVE numbers, will see an even greater challenge when it comes to providing an accurate view of the real risk their business may be living with and the overall vulnerability management landscape.
As a side note, we’re also seeing challenges facing the National Vulnerability Database which effectively stopped analysing vulnerabilities in February 2024. As you can imagine, the backlog of CVE’s awaiting analysis rapidly grew but the industry as a whole is stepping up. NVD have announced new partnerships and processes to improve their efficiency, and hopefully they’ll be able to meet their own deadline of the end of 2024 to clear the CVE backlog.
2. CISA KEV Is A Fantastic Starting Point, But Won't Provide Full Coverage
Throughout Q2, Cytidel intelligence automatically assigned 39 unique CVEs with risk rating of "Significant" due to intelligence collected such as exploits, proof-of-concepts, threat campaigns, or news and social mentions.
From that list of 39 CVEs, 5 (13.5%) were not included on CISA KEV list despite reports of exploitation in the wild.
Let's look at CVE-2024-28255 for example. In April, Microsoft Threat Intelligence identified an attack campaign targeting Kubernetes clusters running the popular open-source metadata platform, OpenMetadata.
At-a-glance timeline:
- March 15th:
- CVE first identified
- April 2nd:
- Cytidel intelligence picked up a potential proof-of-concept
- April 19th:
- First reports of active exploitation
- Trended across news and social media
- May 25th:
- Additional proof-of-concept identified
- June 26th:
- Additional proof-of-concept identified
Here's the 5 CVEs associated with active exploitation attempts that are not on the CISA KEV catalog.
| CVE | Vendor | Context |
|---|---|---|
| CVE-2024-28255 | OpenMetadata | Reports of this vulnerability being exploited in the wild and multiple POCs |
| CVE-2024-5806 | Progress | Reports of exploitation in the wild and POC found |
| CVE-2024-2961 | GNU C Library | Reports of this vulnerability being exploited in the wild and large amount of POCs |
| CVE-2024-26234 | Microsoft | Zero Day confirmed by Microsoft as being actively exploited in the wild |
| CVE-2024-1800 | Progress | Not directly exploited. However, chained with actively exploited CVE-2024-4358 to achieve a full unauthenticated RCE. Plus, multiple POCs found. |
3. 56% Of The Top Q2 Risks Have An EPSS Under 3%
Before we go further, it would be remiss of us not to say that we are big fans of Exploit Prediction Scoring System (EPSS). Like CISA KEV, EPSS can be a great starting point for analysts or organisations looking to prioritise and work through their vulnerability backlog. There is no doubt that when you see a CVE with greater than 90% EPSS, you need to act.
However, EPSS despite being positioned as a predictive score, can at times be a lagging indicator. Often taking days, if not weeks (or longer), for the EPSS score to catch up on real world exploit intelligence.
Throughout Q2, Cytidel Intelligence identified 39 unique vulnerabilities with a Significant Risk Rating. Of these 39 CVEs, 22 have an EPSS under 3%. That's despite 20 of these being tagged by our intelligence as a potential zero day or actively exploited, and 18 CVEs associated with at least one proof-of-concepts.
To go even further, 6 of the 22 CVEs with a below 3% EPSS score are even associated with known threat actors.
Take CVE-2024-20359 as an example, a vulnerability associated with a sophisticated cyber-espionage campaign, known as "ArcaneDoor," that targeted Cisco firewall devices globally.
At-a-glance timeline:
- April 24th:
- First identified
- Added to CISA KEV
- Added to Cytidel Spotlight
- Cytidel Risk Rating rose to High
- April 25th
- Trended on news and social media
- EPSS of 0.13% assigned
- May 1st
- Cytidel Risk Rating rose to Significant
- May 6th
- Proof-of-concept identified
As you can see, an EPSS score of 0.13% was added on the 25th, despite reports of active exploitation from nation state threat actors. The score has remained static since.
Here's the 6 CVEs associated with known threat actors but have an EPSS below 3%.
C V E | Vendor | EPSS | Associated Threat Actors & Aliases |
Cisco | 0.13% | UAT4356
| |
Microsoft | 0.06% | Black Basta | |
Microsoft | 0.05% | Fancy Bear
| |
Cisco | 0.28% | UAT4356
| |
Microsoft | 0.46% | Narwhal Spider
| |
Linux | 1.05% | ExCobalt |
4. Some Vulnerabilities Trend Before Being Published To NVD
Throughout April, May and June we noticed a handful of CVEs trending across news and social that were not yet published to NVD. Quite often the impact of this is negligible for companies, but from time to time a vulnerability comes along that Cytidel Intelligence recommends remediating days before the CVE is published to NVD.
The reality of this means that organisations cannot be entirely dependent on vulnerability scanners to report their total exposure. They will need to incorporate threat intelligence into their vulnerability management programs to avoid scenarios whereby a major vulnerability is under exploit, but may not appear on their scanners for days.
CVE-2024-4577, one of our top 12 vulnerabilities of Q2 was on our radar for three days before it was eventually published to NVD.
At-a-glance timeline
- June 6th
- Identified by Cytidel
- June 7th
- Proof-of-concept identified
- Added to Cytidel Spotlight
- Began trending on news and social media
- Cytidel customers advised to patch or implement outlined temporary measures
- June 9th
- Published to NVD
- June 10th
- Nuclei Template added
- June 11th
- Multiple POCs added
- Confirmed reports of TellYouThePass ransomware exploiting the CVE
- June 12th
- Added to CISA KEV
5. Time From Identification To Active Exploit Is Reducing
In June, Progress MOVEit Transfer was back in the news when a number of vulnerabilities were disclosed and trended across news and social. Perhaps the most interesting of these was CVE-2024-5806, which Dark Reading reported as being under attack mere hours after it was disclosed.
At-a-glance timeline:
- June 24th
- CVE first identified
- Proof-of-concepts identified
- June 25th
- First reports of active exploitation
- June 26th
- Trended across news and social media
Very shortly after vulnerability details were published today we started observing Progress MOVEit Transfer CVE-2024-5806 POST /guestaccess.aspx exploit attempts. If you run MOVEit & have not patched yet - please do so now: https://t.co/AenLgqg1wM
— The Shadowserver Foundation (@Shadowserver) June 25, 2024
NVD: https://t.co/OHQRNFNE9p
This example is unlikely to be an anomaly, highlighting the increasingly opportunistic nature of attackers.
Just a couple of years ago when Cytidel was getting started, it was reported that hackers were responding to new vulnerabilities 3x faster than businesses, and that the average time to known exploitation was just 12 days. That was 2022, and at the time it was a 70% reduction in response time from the previous year. Fast forward to 2024, and this would represent a greater than 90% reduction is response time if this behaviour was to become the norm.
Follow us on LinkedIn where we post weekly Spotlight CVEs, and get notified when our blog posts are published.




